User Records
General
How does Alma manage user records?
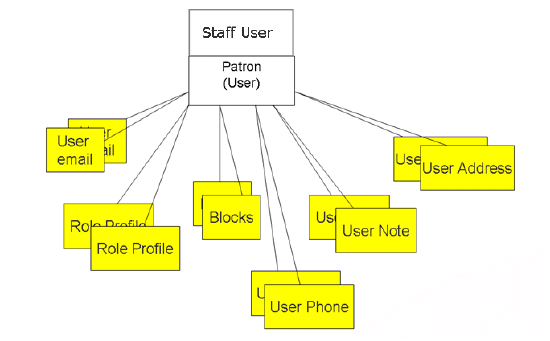
- Internal – An internal user is one whose core user details are managed within the system (for example, user name, contact information, and so on).
- External – With this account type, users are created by migration from an external system. The core user details are managed in an external system where the core details can be viewed but not edited. The users’ information is loaded into Alma and synchronized on a regular basis. It is possible to update an external user’s information manually in Alma, but these updates are overridden by the next synchronization with the user information system. Authentication of external users is performed outside of Alma—for example, in LDAP.
How does Alma manage users who are not part of the university?
In Alma “internal users” are users who are created and managed in Alma, rather than an external system such as a Student Information System.
Internal users can be authenticated using social login or email-based login. In addition, Alma supports the option of adding passwords to internal users. In this case, the password will be stored in the “Ex Libris Identity Service”: a commercial, best-of-breed identity provider application hosted by Ex Libris in its data centers. Library staff can manage passwords for internal users from within Alma. Passwords managed in Alma are stored in the Identity Service. When a user is deleted or purged from Alma, the password is removed from the Identity Service.
Only the user’s password will be stored in the “Ex Libris Identity Service”. All other data is part of the user’s record in Alma.
Does Alma support social login?
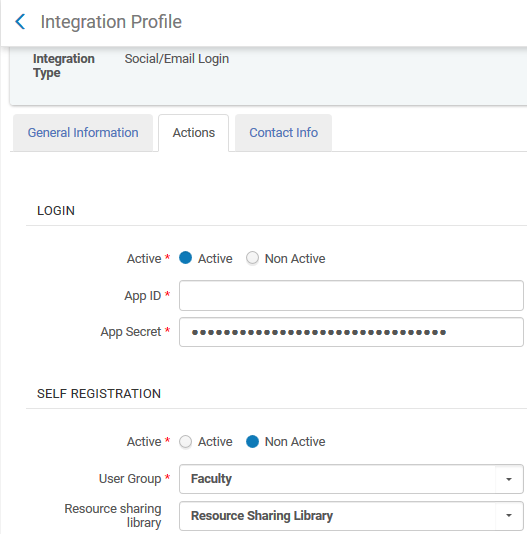



Can a user account be locked after a number of failed logins?
Alma implements a security feature that locks out a user who attempts to log on more than a defined number of times.
It is possible to define:
1. Number of allowed login attempts (supported values are between 3-20 attempts).
2. Lock duration (supported values are between 3-20 minutes).
Authorized staff users can unlock the account.
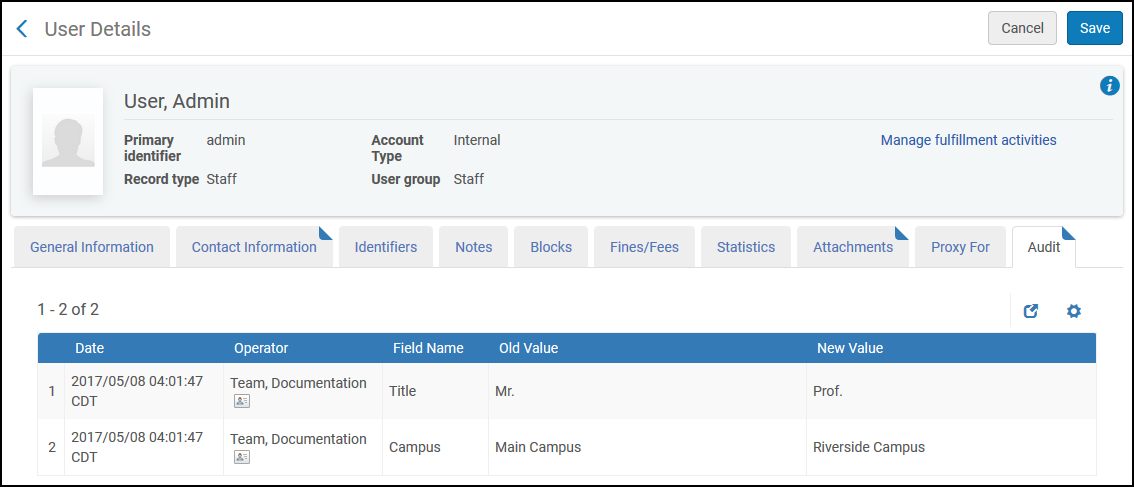
Does Alma maintain an audit trail of changes made to a user record?
Changes made to the user are recorded in the Audit tab of the User Details page. In addition to tracking changes made in the Alma UI, changes made by SIS, APIs, linked account refreshes, and the Update/Notify Users job are also captured.
Can user records be purged?

Can a retention period for letter attachments be defined?
Letter attachments are retained in Alma for a certain length of time; this length can be defined per letter. After the defined retention period, an attachment is permanently deleted. The mapping table Letter Retention Configuration lists letters and the number of days the letter is retained before auto-deletion. A weekly job deletes all attachments for the listed letters that were created prior to the retention date.
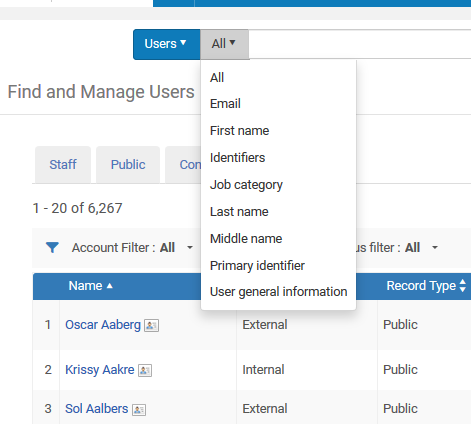
What search options are available on the user file?
Search for users is available from Alma’s user interface using the following fields: General information, Email, Identifier, First name, Last name, Middle name, Job category, Primary identifier:
Passwords
What options are there for managing user passwords?
-
Use of SAML-based SSO authentication
-
Use of CAS based SSO authentication
-
LDAP based authentication
-
OAuth based Authentication with systems - Google, Facebook and Twitter
-
Email based one time authentication
Institutions that do not have an institutional identity provider may use the Ex Libris Identity Service. For more information on the Ex Libris Identity Service, see here.
Staff authorizations
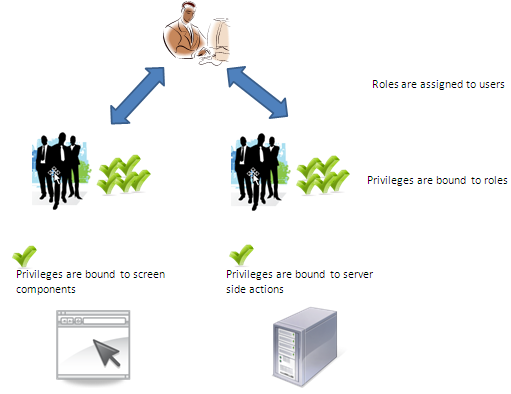
How are authorizations managed in Alma?
- What menus are displayed to the user
- What screens are accessible for the user
- What tables/lists/forms are accessible to the user
- What actions are allowed within screens
- What system jobs are allowed to be triggered by the user
-
Institutional scope – Role with an institutional scope is granted relevant privileges in the entire institution.
-
Library scope – Role with a library scope is granted relevant privileges only within the scope’s library.
How are staff authorizations handled?
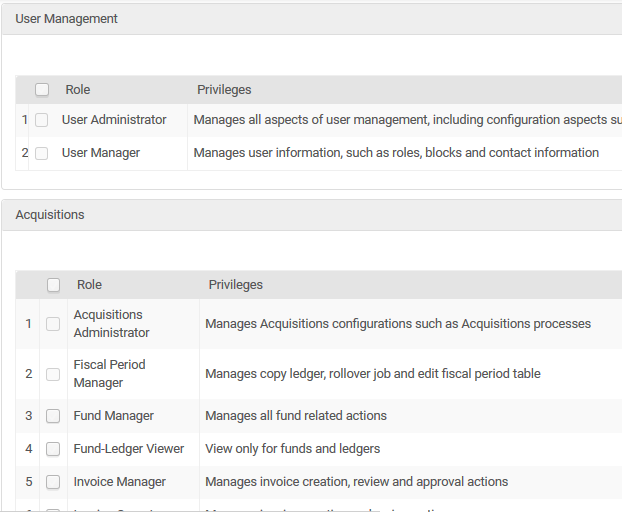
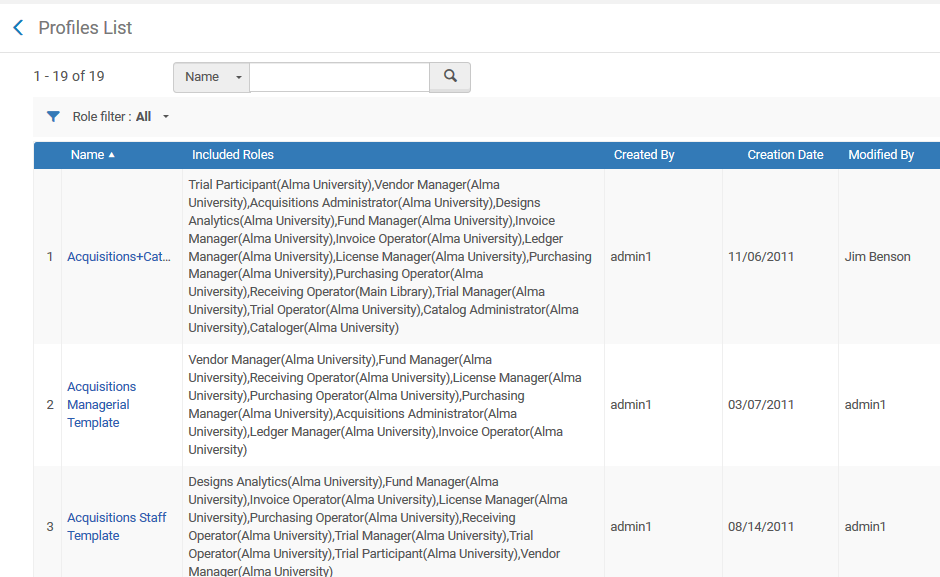
Can profiles of permissions be created?
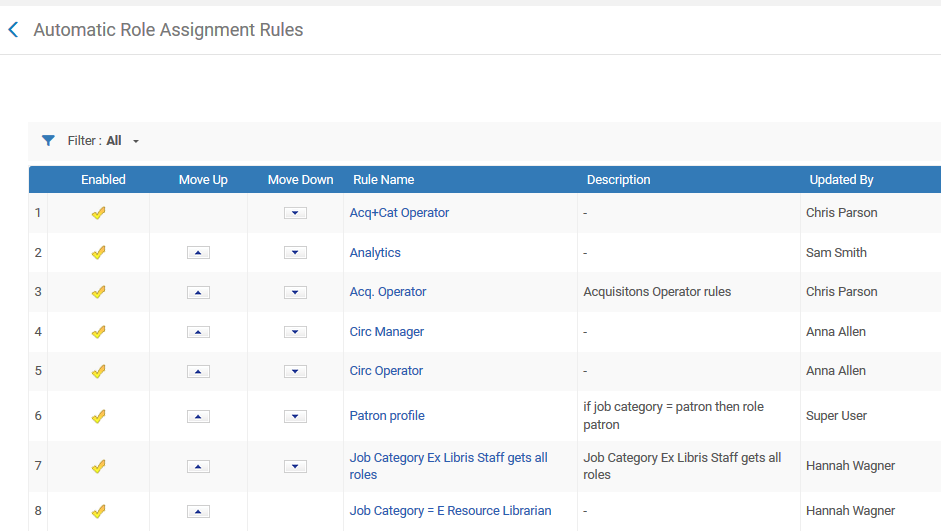
Is automatic role assignment supported?
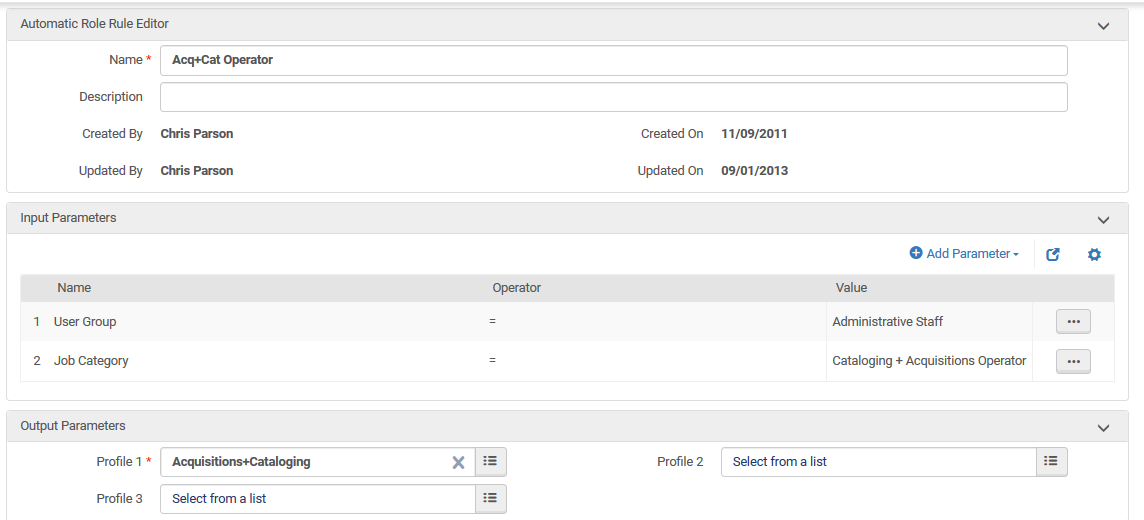
Can roles be easily assigned?
- Role profiles are bundled together role and role scopes that may be assigned in a single action. When creating a new user in the system, a role profile may be assigned to the user, effectively assigning all of the roles and scopes of that profile to that user
- Role Assignment Rules – Rules may be set up for automatically assigning role profiles to newly created/imported users, based on user record attributes such as job category and job description or user group. Any user imported or manually created in the system will have the role that is bundled in role profiles automatically assigned if the user’s attributes match the rule parameters.
Can roles be set at the library level?
-
Institutional scope – Role with an institutional scope is granted relevant privileges in the entire institution.
-
Library scope – Role with a library scope is granted relevant privileges only within the scope’s library.
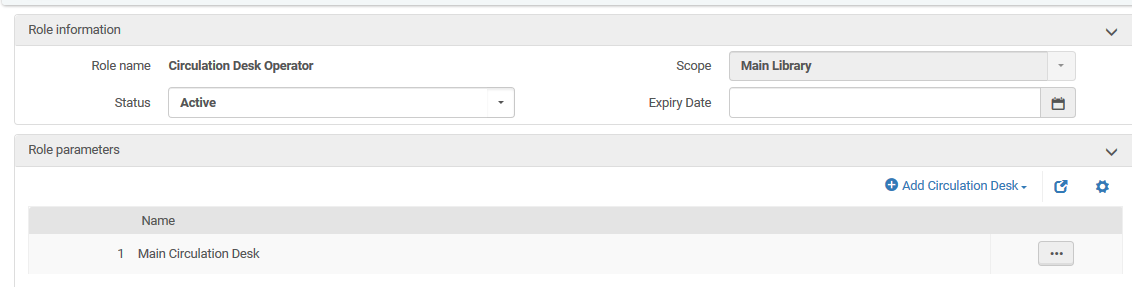
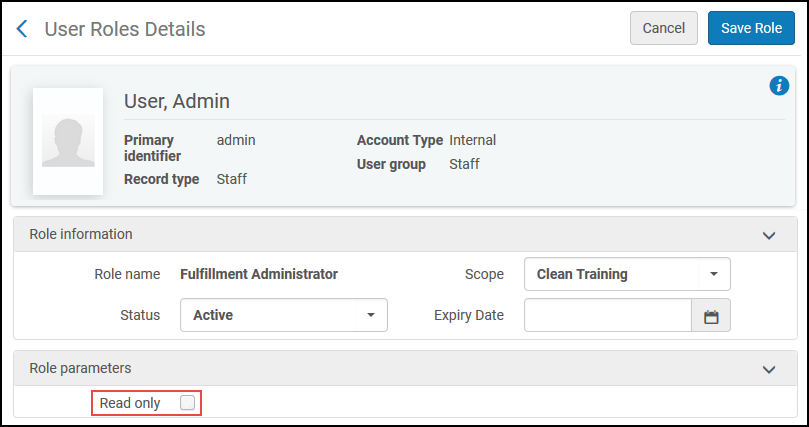
Are view only roles supported?
Fulfillment, User, Catalog, Repository, and Acquisitions Administrator roles can be set so that they can view but not edit configuration settings. A 'Read Only' check box on the role will disable edit functions for this role:
Does Alma allow for administrative and functional authorization at multiple levels?
- Staff members must authenticate prior to accessing Alma
- Each staff member has privileges and access to data limited to his/her role
- Alma’s browser sessions are encrypted using SSL.
- Menu options
- Screen lists/tables/forms/buttons
- Server side actions
What granularity is available regarding roles and privileges?
-
Required privileges are bound to entities such as:
-
Menu options
-
Screen lists/tables/forms/buttons
-
Server side actions
-
-
Roles bind privileges, so that assigning a role to user is equivalent to granting the user all of the privileges that are bound to that role;
-
Only users who have roles mapped to the required privileges will have access to the relevant menu/screen elements/server side actions.
-
Manually create a new order
-
Review and update an order
-
Send the order to the vendor
-
Approve orders that have been identified by the system as requiring special approval, as per institutional criteria
-
Delete an order. Being allowed to perform this action would require an addition extended role
-
Approve invoices
-
Delete Invoices
- Purchasing Operators
- Invoice Operators
Total views:
5567
