Technical Requirements for Alma and Discovery Implementation
The Alma Cloud Deployment Model
FedRAMP customers: the FedRAMP IP ranges are not listed in the IP range section, but the information in the rest of the document is still applicable.
Making the Cloud Vision a Reality
True Multi-Tenancy
Vendor-Managed Updates
Seamless Integration/Open Platform
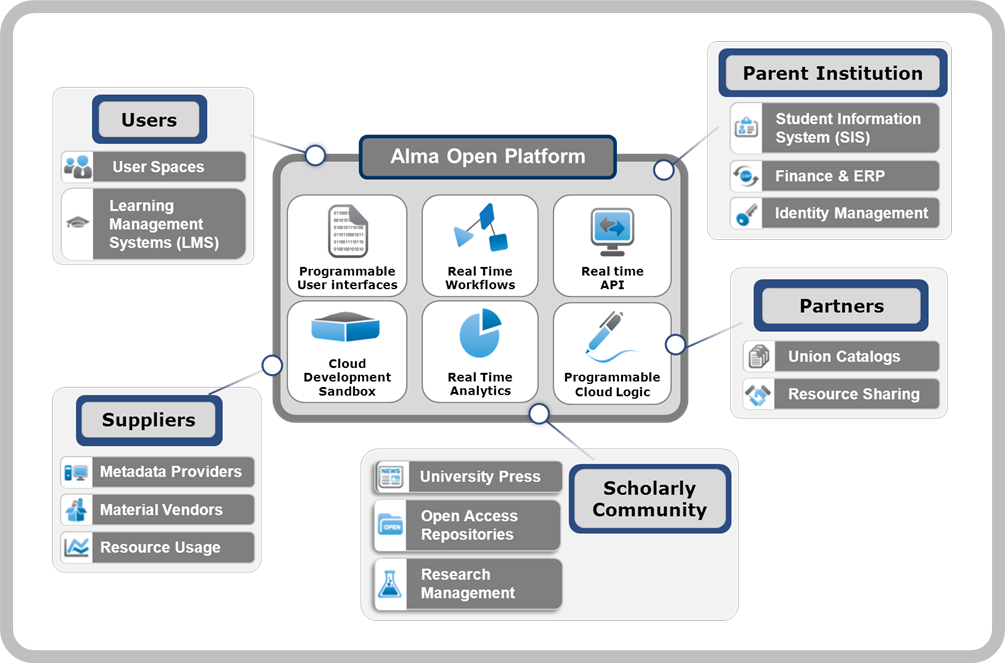
Security
Performance and Service Availability
Network Communication
Browser Communication
Network Communication
Higher-Ed Platform IP Range
- In the U.S.A. (refers to the NA01, NA02, NA03, and NA04 instances on the Chicago data centers and the NA05, NA06, NA07 and NA08 instances on the Seattle data centers):
- 66.151.7.40/29 [66.151.7.40-47]
- 66.151.7.128/26 [66.151.7.128-191]
- 66.151.7.192/28 [66.151.7.192-207] - Note that 66.151.7.202 is to enable calls from the Community Zone.
- 66.151.7.224/30 [66.151.7.224-227]
- 66.151.7.236
- 66.151.14.128
- 66.151.14.129
- 74.217.12.128/27 [74.217.12.128--159]
- 64.74.237.221
- 64.74.237.229
- 64.74.237.232/31 [64.74.237.232-233]
- 216.147.208.128/26 [216.147.208.128-191]
- 216.147.209.0/27 [216.147.209.0-31]
- 216.147.212.20/30 [216.147.212.20-23]
- 216.147.212.25
- 216.147.212.64/26 [216.147.212.64-127]
- 216.147.212.128/27 [216.147.212.128-159]
- 216.147.212.21
- 216.147.212.30
- 64.74.237.220
- 64.74.237.229
- In Canada (refers to the Ex Libris Canadian data center):
- 216.147.222.64/29 [216.147.222.64-71]
- 216.147.222.128/29 [216.147.222.128-135]
- 216.147.222.124/30 [216.147.222.124-127]
- 216.147.222.188/30 [216.147.222.188-191]
- 216.147.222.30
- In Europe (refers to the EU00, EU01, and EU02 instances on the Amsterdam data centers and the EU03, EU04, EU05, and EU06 instances on the Munich data centers):
- 95.172.90.160/27 [95.172.90.160-191]
- 31.186.254.128/28 [31.186.254.128-143]
- 216.147.214.128/26 [216.147.214.128-191]
- 216.147.218.128/26 [216.147.218.128-191]
- 216.147.218.64/26 [216.147.218.64-127]
- 216.147.215.0/27 [216.147.215.0-31]
- 95.172.88.57
- 216.147.218.253
- In APAC (refers to the AP01 instance on the Singapore data center and the AP02 instance on the Sydney data center):
- 117.20.42.16/31 [117.20.42.16-17]
- 117.20.42.32/27 [117.20.42.32-63]
- 117.20.42.137
- 216.147.220.128/29 [216.147.220.128-135]
- 216.147.220.64/28 [216.147.220.64-79]
- 216.147.221.64/28 [216.147.221.64-79]
- 216.147.221.96/28 [216.147.221.97-110]
- 216.147.221.192/28 [216.147.221.192-206]
- 117.20.42.12
- 216.147.221.253
- In China (refers to the Ex Libris Beijing data center):
- 124.251.9.0/26 [124.251.9.0-63]
- 124.251.9.15
Access to the above IP ranges may require firewall settings at the institution level and inclusion in the institution's SPF DNS record (in order to avoid Alma emails potentially being handled as spam).
Primo Classic IP Range
- In the U.S.A.:
- 64.74.237.229 (MT NA01 and TC NA)
- 66.151.7.8 (MT NA02)
- 66.151.7.11 (MT NA03)
- 66.151.7.55 (MT NA04)
- 66.151.7.235 (MT NA05)
- 64.74.237.218 (MT NA sandbox)
- 216.147.208.160/27 [216.147.208.160-191]
- 216.147.209.32/27 [216.147.209.32-63]
- 216.147.212.20/30 [216.147.212.20-23] (SMTP Mail Gateway)
- 216.147.212.25 (S/FTP)
- 216.147.212.128/27 [216.147.212.128-159] (MT NA05 and TC NA sandbox)
- 66.151.7.63 – proxy-na.hosted.exlibrisgroup.com
- 64.74.237.200 – primo-instant-na.hosted.exlibrisgroup.com
- In Canada:
- 216.147.222.112 (MT CA01)
- 216.147.222.177 (MT CA01 sandbox)
- 216.147.222.177 (CA01 implementation)
- In Europe:
- 31.186.254.144 (MT EU01)
- 31.186.254.179 (MT EU02)
- 31.186.254.228 (MT EU03)
- 31.186.254.96 (MT EU04)
- 31.186.254.152 (TC EU)
- 95.172.90.146 (MT EU sandbox)
- 216.147.218.96/27 [216.147.218.96-127]
- 31.186.254.83 – proxy-eu.hosted.exlibrisgroup.com
- 95.172.90.153 – primo-instant-eu.hosted.exlibrisgroup.com
- In APAC:
- 117.20.42.20 (MT APAC)
- 117.20.42.129 (MT APAC03)
- 117.20.42.134 (TC APAC)
- 117.20.42.134 (TC APAC02)
- 117.20.42.162 (MT APAC sandbox)
- 216.147.221.96/28 [216.147.221.96-111]
- 117.20.42.224 – proxy-ap.hosted.exlibrisgroup.com
- 117.20.42.136 – primo-instant-apac.hosted.exlibrisgroup.com
- In China:
- 124.251.9.21
- 124.251.9.33 (sandbox)
- 124.251.9.34 (implementation)
Primo VE IP Range
- In the U.S.A.:
- 66.151.7.63 – proxy-na.hosted.exlibrisgroup.com
- 64.74.237.200 – primo-instant-na.hosted.exlibrisgroup.com
- In Europe:
- 31.186.254.83 – proxy-eu.hosted.exlibrisgroup.com
- 95.172.90.153 – primo-instant-eu.hosted.exlibrisgroup.com
- In APAC:
- 117.20.42.224 – proxy-ap.hosted.exlibrisgroup.com
- 117.20.42.136 – primo-instant-apac.hosted.exlibrisgroup.com
Library Open Workflow
- In North America:
- 64.74.237.30 – na-workflows.hosted.exlibrisgroup.com
- In Europe:
- 95.172.90.30 – eu-workflows.hosted.exlibrisgroup.com
- In APAC:
- 216.147.220.208 – ap-workflows.hosted.exlibrisgroup.com
Summon IP Range
Bandwidth Requirements
| Number of Alma Named Users | Required Minimum Network Bandwidth |
|---|---|
| Up to 50 | 0.025 MB per user |
| Above 50 | 0.015 MB per user |
| Above 200 | 0.01 MB per user |
- 10 Alma named users = 0.25 MB
- 500 Alma named users = 5 MB
Alma-Primo
This section is not relevant to Primo VE, which is deployed on the Higher-Ed platform.
Ex Libris Primo customers that are also Alma users work with Primo in the Ex Libris cloud and thus benefit from a complete cloud environment and smooth updates of both solutions. Alma and Primo communicate within the Ex Libris cloud network and the only external communication is between patrons and Primo functions over port 80 or 443.
If you have PCs in your institution that are open only to specific servers and ports (and specifically to Primo), make sure that these PCs/firewalls are also open to the Alma server and port.
If the customer is using on premises / local Primo deployment, Alma communicates with Primo in a bi-directional manner, as follows:
-
Alma to Primo: an OAI-PMH XML of published metadata is sent from Alma to Primo via Secured FTP over ports 21/22
-
Alma-Primo: bi directional HTTPS communication of patron services over port 443
For more information on Alma-Primo integration, refer to the Alma-Primo Integration Guide.
Alma-Primo Patron Services
Primo Back Office
This section is not relevant to Primo VE, which is deployed on the Higher-Ed platform.
Alma-MetaLib (when MetaLib is in use)
Alma-Summon
Alma-Summon Patron Services
Summon Admin Console
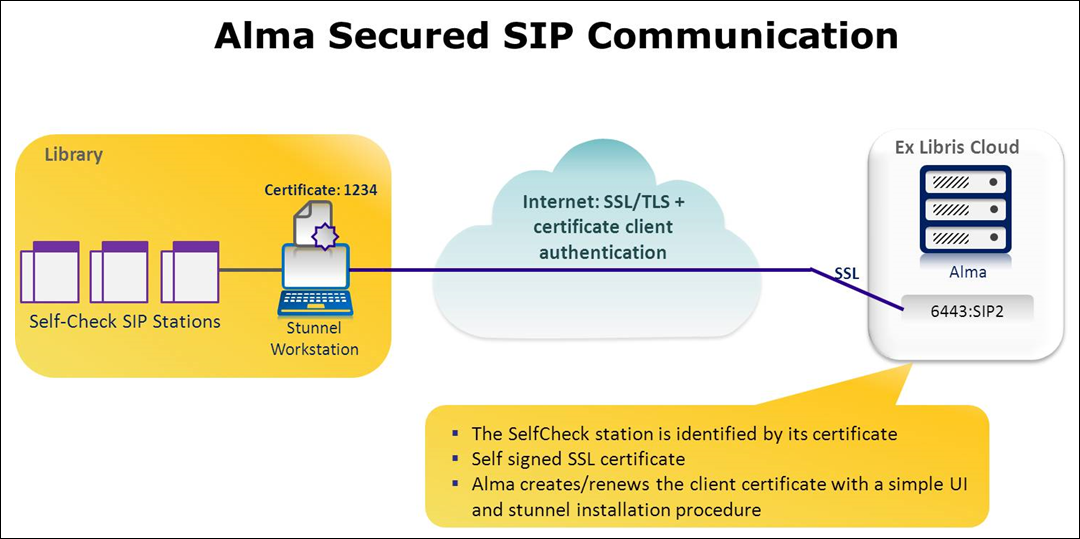
Alma – Self-Check Machines/SIP-based Systems
- The SIP2 local machines communicate with Stunnel software that is installed on the local Windows/Linux workstation.
- The Stunnel encryption component encrypts the TCP communication using a standard encryption method and a security certificate, and will send the SIP2 requests to the Alma cloud over the secure port 6443.
Alma – Financial/SIS Systems/Vendor EOD, EDI/SMS (File-Based)
OCLC Connexion
Resource Sharing (ILL)
Data Providing
Digital Resources
Alma Authentication
Printers
- Print to a locally defined PC printer, via the Alma Print Queue. For more information, see The Printout Queue and Quick Printing in Alma.
- Email and corresponding printing rules
- Each library/institution defines the email addresses of its local printers in Alma, which route staff-oriented, Alma-originating e-mails (including request and transit slips) to the appropriate printer.
- Newer printers have their own built-in email addresses to support cloud computing. If you are using a new printer, therefore, the email address for notifications should be the printer’s email address.
- Older printers do not support direct emailing and will therefore require a print proxy. There are several applications available to manage printer routing. For example:
- MS Outlook printing rules – It is possible to create an email address and link this address to a printer via your MS Outlook printing rules.
- Automatic Email Manager (AEM) by Namtuk – For details, see http://www.namtuk.com/
The above are examples only. Any print proxy that meets your institution's needs can be used.
Emails
- The SMTP Envelope-From address is used only by the mail server.
- The email’s message header From: address is used primarily by the email client (such as Outlook or Thunderbird). It may also be looked at by anti-spam filters.
- The customer wants all emails sent on their behalf to be branded with their own domain.
- The customer wants to receive bounce emails (automatic notification of non-delivered emails) directly to a mailbox on their own mail server.
- The customer must change EnvelopeFrom to a valid mailbox in the customer’s domain, for example library-bounce@cust_domain.edu.
- The customer must change the message header From: addresses in relevant Alma letters to addresses in the same domain used for EnvelopeFrom, for example library-noreply@cust_domain.edu. These addresses do not have to be valid mailboxes.
Mail Relay Gateways
|
Region |
SPF Include Record |
IPs/IP Ranges |
|---|---|---|
|
APAC |
include:spf-ap.exlibrisgroup.com |
117.20.42.8/29 (117.20.42.8 - 15) 216.147.221.8/31 (216.147.221.8 - 9) |
|
Canada |
include:spf-ca.exlibrisgroup.com |
216.147.222.12/30 (216.147.222.12 - 15) |
|
China |
include:spf-cn.exlibrisgroup.com.cn |
124.251.9.14/31 (124.251.9.14 - 15) |
|
North America |
include:spf-na.exlibrisgroup.com |
64.74.237.230/31 (64.74.237.230 - 231) 216.147.212.20/30 (216.147.212.20 - 23) |
|
Europe |
include:spf-eu.exlibrisgroup.com |
95.172.90.143 95.172.90.156 216.147.218.8/30 (216.147.218.8 - 11) |
Network Communication Diagram and Table
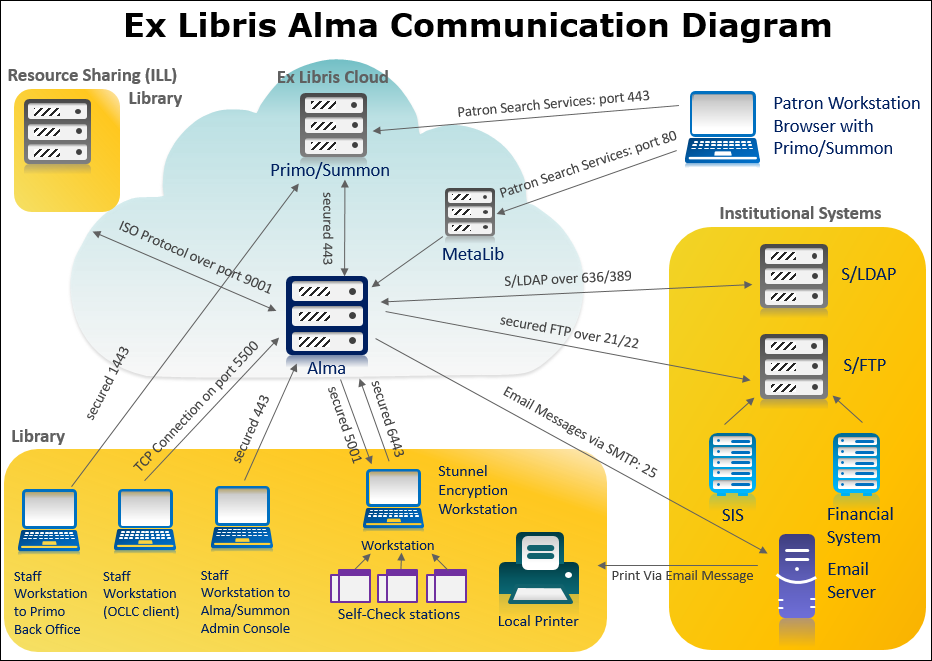
| Integration Type | Initiator | Target | Protocol | Ports | Comments |
|---|---|---|---|---|---|
| Staff workstation | Staff workstation | Alma | HTTPS | 443 | |
| Staff workstation | Primo (Back Office) | HTTPS | 1443 (multi-tenant) | ||
| Staff workstation | Summon Admin Console (via Alma) | HTTPS | 443 | ||
| Patron workstation | Patron workstation | Primo | HTTPS | 443 | |
| Patron workstation | Summon | HTTPS | 443 | ||
| Staff authentication | Alma |
CAS (SSO)
SAML (SSO)
Social Login
|
HTTPS | 443 | |
| Secure LDAP | TLS-Secured | 636 | |||
| Alma-Primo | Primo | Alma | HTTPS | 443 | |
| Primo Central | Alma | HTTPS | 443 | Primo central registration with Alma URL | |
| Alma-Primo end-user authentication | Primo | CAS (SSO)
SAML (SSO)
Social Login
|
HTTPS | 443 | |
| Secure LDAP | TLS-Secured | 636 | |||
| Alma-Summon | Summon | Alma | HTTPS | 443 | |
| Alma-Summon end-user authentication | Summon (via Alma) | CAS (SSO)
SAML (SSO)
Social Login
|
HTTPS | 443 | |
| Secure LDAP | TLS-Secured | 636 | |||
| Alma | Email Server | SMTP | 25 | Print via email messages | |
| S/FTP file-based integrations (outgoing) | S/FTP Server |
|
S/FTP | 21/22 | |
| S/FTP Server | Publishing platform - Summon | S/FTP | 2022 | ||
| S/FTP file-based integrations (incoming) |
|
S/FTP Server | S/FTP | 21/22 | |
| Ex Libris APIs (for more information, see the Developer Network) |
Client applications
|
Alma | HTTPS | 443 | |
| Remote storage (for file-based remote storage, see S/FTP file-based integrations - outgoing above) | Stunnel workstation (Dematic ASRS remote storage facility system) | Alma | TLS-secured | 6443 | Using Stunnel |
| Alma | Stunnel workstation (Dematic ASRS remote storage facility system) | TLS-secured | 5001 | Using Stunnel | |
| Self-check | Stunnel workstation (SIP2 Self-Check Stations) | Alma | TLS-secured SIP2 | 6443 | Using Stunnel |
| Resource sharing (ILL) system (Alma or non-Alma) | Peer to peer resource sharing (ILL) system | Alma | TCP | 9001 | |
| Alma | Peer to peer resource sharing (ILL) system | TCP | 9001 | ||
| Broker resource sharing (ILL) system | Alma | HTTPS | 443 | ||
| Alma | Broker resource sharing (ILL) system | HTTPS | 443 | ||
| RFID | Alma | RFID driver installed on a user's PC | HTTP | Determined by user | For more information on port configuration, see the Developer Network. |
| OCLC Connexion | OCLC Connexion | Alma | TCP | 5500 | Accelerated servers are not supported. |
| Google Scholar and other third-party electronic service providers | Electronic service provider | Alma (via Discovery) | HTTP or HTTPS | 80 or 443 | Via Discovery services page directed to Alma’s delivery services |
| Z39.50 data providing | Z39.50 server | Alma | TCP | 1921 or 210 | 210 is open on all production environments; sandbox environments support only 1921 |
| OAI-PMH data providing | OAI | Alma | HTTPS | 443 | |
| SRU-SRW data providing | SRU-SRW | Alma | HTTPS | 443 | |
| Aleph Central Catalog for Aleph contribution | Alma | Aleph | HTTP or HTTPs | Institution-specific port definition | |
| Aleph Central Catalog for Aleph bibliographic record updates | Alma | Aleph | TCP | Institution-specific port definition | |
| Aleph Central Catalog for Aleph retrieving bibliographic records (external search) | Alma | Aleph | TCP | Institution-specific port definition | |
| Aleph Central Catalog for SBN contribution | Alma | SBN | HTTP | Institution-specific port definition | |
| Aleph Central Catalog for SBN retrieving bibliographic/authority records (external search) | Alma | SBN | HTTP | Institution-specific port definition | |
| Electronic access proxy (EZProxy, etc.) | Alma | Proxy | HTTPS | 443 | |
| Webhooks | Alma | External server | HTTPS | 443 | |
| Deposit using SWORD | Alma | Alma SWORD server | HTTPS | 443 | |
| Online payment | Alma | WPM education system | HTTPS | 443 | |
| Primo | WPM education system | HTTPS | 443 | ||
| Learning Tools Interoperability (LTI) | Course management system | Alma | HTTPS | 443 |

