Managing Token-Based Authentication
Overview
campusM Authentication (CMAuth) is a standardized token-based authentication mechanism and framework that seamlessly supports the handshake, validation, and mapping attributes for authenticated users offering a variety of possible integrations with systems supporting the following protocols:
- SAML2
- OAuth2/OIDC
- LDAP
- Alma
- Connect Layer
- Alma Social Login
- CAS
The campusM authorization token is implemented as a signed JWT (JSON Web Token) and is used exclusively by campusM across the campusM components (Cloud, Connect Layer) to ensure appropriately authorized users within the app. This is not to be confused with the standard IdP authorization token which is managed by a standard browser-session cookie.
Token Expiry and Best Practice
The expiry lifetime of the campusM auth token is 30 days by default. (This is configurable.) This determines how often the user needs to re-authenticate to use the campusM app. This may be set differently for Web and native/mobile, if necessary.
The campusM authorization token is different from the browser-cookie stored token used by the IdP system for single sign on to other systems and should not be confused. Typically, the IdP expiration is configured to be much shorter (a few hours or days) than the campusM-specific auth token.
Tokens for Other IdP-Based Systems
campusM users can access external systems with a product integration or a link-out with single-sign-on functionality. This requires that the IdP token cached on the user’s browser is not expired. (The expiration of this token is set by the University’s IdP administrator). When expired, the user may need to re-authenticate to access specific external systems.
Some integrations require an additional unique trusted handshake between systems whereby a special third-party application token may be generated upon the user’s first access and then cached locally for that user and used securely for subsequent access from that device.
Since the campusM auth token itself is never used outside of campusM, it is not used for interfacing with external systems. However, since the campusM auth token may store optional attributes mapped from the IdP, those details can be retrieved for use in communications such as API calls with other external systems with which campusM interfaces. Such mappings can be useful for scenarios where that information is needed to communicate with other systems. For instance, a library integration may identify an end user by a different username than the username in campusM. With attribute mapping, if the IdP passes the additional attribute then it can be retrieved and used when communicating with the library system’s API, even though the username in campusM is different.
For OAuth2/OIDC there is also an option to use the access token returned during the login process to store optional attributes. Though similarly to IdP sessions, the campusM token lifetime is not tied to the expiration of the OAuth access token, but it can be configured to equal it. In cases where refresh tokens and expiration times are supplied along with access tokens, the refresh tokens can be used to automatically refresh the access tokens when needed. Note that these tokens are kept encrypted on the campusM token and therefore, it is recommended to keep these tokens limited to a reasonable size since they are sent with each request.
Two-Factor Authentication
Two-factor authentication (TFA) is supported as part of campusM solution as long as they are managed by the authentication system external to campusM. The campusM auth token generation and IdP token generated by the IdP should be agnostic to the TFA setup by your institution.
Configuring CMAuth
Perform the following to configure CMAuth:
- Configure an integration profile. For information on how to configure the integration profile for each one of the protocols, see Configuring Integration Profiles.
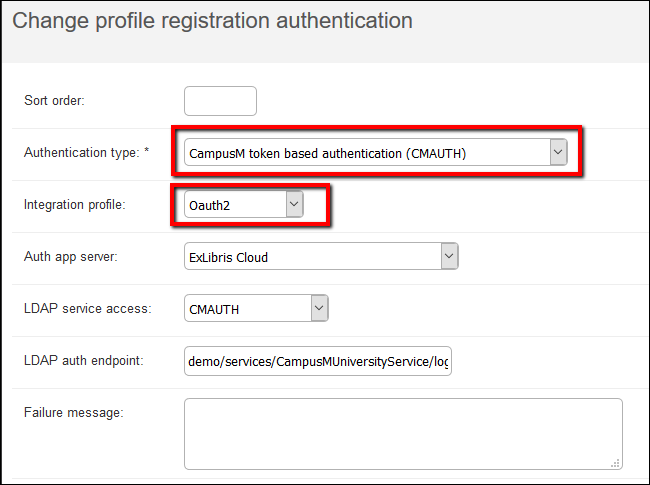
- From profile registration authentication (App Manager > App Settings > Profile Registration Authentication):
- Select CMAuth.
- For the Authentication type field, select CampusM token-based authentication (CMAUTH).
- For the Integration profile field, select the integration profile you created.
 Profile Registration Authentication
Profile Registration Authentication


