Step 2: Authentication Profiles
Authentication allows patrons to sign in to Primo VE to access fulfillment services from Alma (such as placing a request). This guide provides information on how to configure various authentication systems and integrate them with Primo VE.
Background
Main Principles and Differences between Primo and Primo VE
Authentication is used the same way in both Primo and Primo VE, but here are their configuration differences:
-
Primo:
Authentication is configured in either PDS or the Primo Authentication Manager and is set up to work with your institutional IDP or Alma internal users.
-
Primo VE:
External authentication is managed and defined using Alma’s integration profiles. An institution may choose to use one or more authentication schemes (such as LDAP, CAS, and SAML).
The authentication profiles and login pages that are used specifically for Primo VE are configured in Alma’s integration profiles and enabled on the User Authentication page under the Discovery configuration menu.
Documentation and Training
In preparation for this task, it is recommended that you familiarize yourself with the following documentation:
Preparation: Checking Your Authentication Schemes in Primo
Before you begin configuration in Primo VE, check to see which sign-in options you are currently using for your patrons in Primo. If you need assistance, consult your institution's IT department since additional tasks may be needed on the institutional IDP to allow Primo VE to authenticate.
Configuration
Configuring authentication in Primo VE requires the following steps:
Creating Integration Profiles for Authentication
Primo VE utilizes Alma's authentication system to define the necessary integration profiles used to support any of the following authentication schemes:
-
LDAP –
-
If you already have an integration profile for LDAP, you may not need to take any further action other than enabling the authentication profile for Primo VE.
-
On the institution’s LDAP, make sure that the firewall allows traffic to and from port 636 on the Primo VE server and that the LDAP server has a valid SSL certificate signed by a trusted CA authority. For more information, see the Certificate List.
-
-
SAML-based authentication (such as Shibboleth) –
-
If you already have an integration profile for SAML, you may not need to take any further action other than enabling the authentication profile on the User Authentication page in Primo VE.
-
If your IDP is Azure, you will need to create an identical integration profile for Primo VE that has an SP-specific signing certificate, which is necessary for Azure.
On the institution’s SAML IDP, you will need to add the Primo VE SP. If there is already an entry for the Alma SP, the new Primo VE entry should have the same metadata (but the word alma must be changed to primo in the entityID, assertion consumer service, and the logout endpoint) and configurations (release the same attributes).
To ensure that end users are logged out in a secure manner, you should add a LogoutURL that properly removes the IDP session.
-
-
CAS –
-
If you already have an integration profile in Alma using CAS, you may not need to take any further action other than enabling the authentication profile for Primo VE.
-
On the institution’s CAS IDP, make sure that the firewall allows traffic to and from port 636 on the Primo VE server and that the CAS server has a valid SSL certificate signed by a trusted CA authority. For more information, see the Certificate List.
-
-
OAuth-based authentication with Facebook, Google, Twitter, or via email using the Social/Email Login Integration Type –
If you already have an integration profile for OAuth, enable its authentication profile on the User Authentication page in Primo VE.
-
Alma internal users with the Ex Libris IDP –
You can enable its authentication profile on the User Authentication page in Primo VE.
For more details on how to configure integration profiles for authentication, see Authentication in Alma.
Enabling Authentication Profiles in Primo VE
The User Authentication page in Primo VE allows you to enable various authentication systems from which to authenticate Primo VE users. For more information, see Configuring User Authentication for Primo VE.
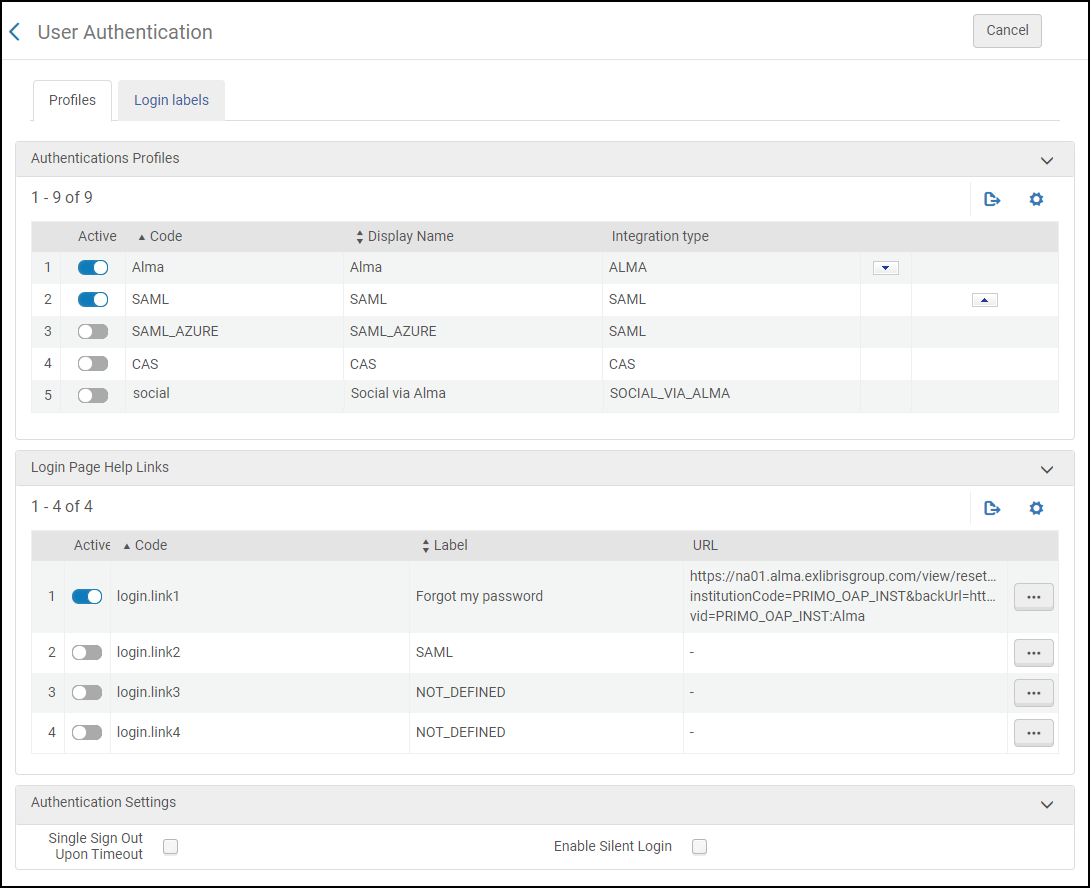
-
Open the User Authentication page (Configuration Menu > Discovery > Authentication > User Authentication).
-
Enable the authentication schemes that you want to support in Primo VE.
-
Specify any other settings, help links, and display labels.
The Enable Silent Login option is not supported if you are using an Azure IDP.
-
Save your changes.

