Using SAML for User Authentication
If you are working with Primo VE and not Primo, see SAML-Based Single Sign-On/Sign-Off.
SAML (Security Assertion Markup Language) is an XML-based, open standard data format for exchanging authentication and authorization data between parties (in particular, between an identity provider and a service provider such as Primo). Primo supports the SAML 2.0 Web Browser SSO profile, which enables Primo to exchange authentication and authorization information.
The SAML specification defines three roles: the user, the identity provider (IDP), and the service provider (SP). Primo is the service provider, and for example, Shibboleth is the identity provider. The following steps describe the interaction between the user, Primo, and the IDP to provide authentication and authorization:
-
The user invokes the sign-in option in Primo.
-
Primo sends an authentication request to the IDP using the HTTP-Redirect binding.
-
The IDP performs a single-sign-on check.
-
If the user is not logged on to the IDP, the IDP’s login page (which is not Primo’s login page) opens.
-
After the user logs on, the IDP redirects back to Primo with a SAML response, which includes an assertion (encrypted or non-encrypted), using the HTTP-POST binding.
-
Primo retrieves the user attributes from the SAML response (or fetches user attributes from Alma or Aleph) and logs the user in.
To configure Primo to use SAML authentication:
-
Gather the necessary information about your IDP provider from your authentication manager. In SAML terms this means to compile IDP metadata.
-
Open the User Authentication Wizard page (Primo Home > Ongoing Configuration Wizards > User Authentication Wizard).
-
Create a new login profile. The Login Profile page opens. For more information on creating login profiles, see The Primo Authentication Manager.
-
Select SAML from the Select Authentication Method drop-down list.The SAML authentication parameters appear on the page.
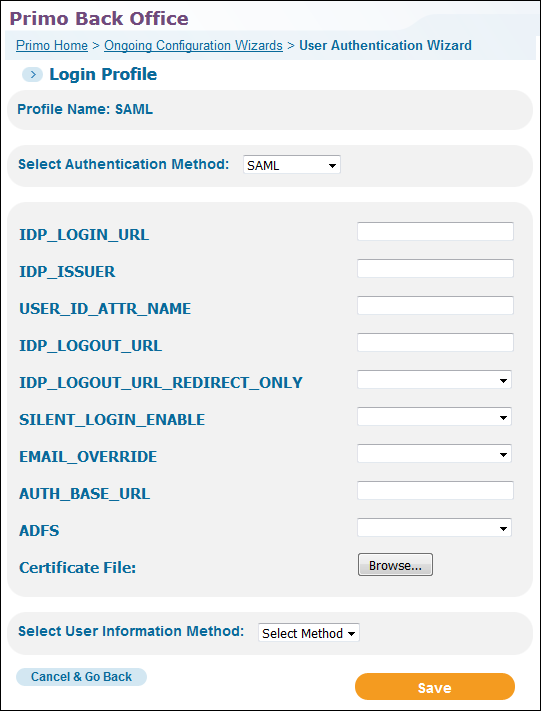 SAML Login Profile Page
SAML Login Profile Page -
Use the following table to configure the SAML authentication parameters:
SAML Configuration Parameters Parameter Description IDP_LOGIN_URL(Required) The IDP login URL. This is the URL Primo uses when it sends the authentication request.IDP_ISSUER(Required) The IDP entity ID.USER_ID_ATTR_NAMEDefines the user attribute that should be used as the user’s unique ID. If not defined, the SAML default will be used.IDP_LOGOUT_URLThis is the sign-out URL. When users sign-out or the Primo session ends, Primo will redirect them to this URL. Depending on the setting of the IDP_LOGOUT_URL_REDIRECT_ONLY field, Primo will also attach a SAML Logout Request to this URL.The IDP logout URL must end with a question mark. For example:https://login.myInst.edu/logout.jsp?IDP_LOGOUT_URL_
REDIRECT_ONLYThis option indicates whether a SAML Logout Request is attached to the IDP logout URL. The following values are valid:-
blank or False – The user is redirected to the IDP logout URL and a SAML Logout Request is attached to the URL so that the logout process can be handled further by the IDP. Check with your Authentication administrator to make sure that this functionality is supported by your IDP provider.
-
True – The user is redirected to the IDP logout URL only.
SILENT_LOGIN_
ENABLEThe valid values are True (default) and False.Enable or disable silent login in Primo. If silent login is enabled and a new session is opened with the same browser in a new window or tab, the user is automatically logged on to Primo.If you have configured multiple authentication profiles, Primo will attempt to apply the silent login with the first eligible profile only.
EMAIL_OVERRIDE
The valid values are True and False (default).If set to True, the email returned with the user information will always override the email stored in the user’s profile in Primo.AUTH_BASE_URLThe base URL name used by the institution. For example:https://<institution>-primo.hosted.exlibrisgroup.comThere is no path after the server name.Use http or https according to your needs.ADFSIndicates whether Active Directory Federation Services (AD FS) is enabled on the system. The valid values are True and False.Certificate File(Required) Click Choose File to select which public encryption key certificate file to load from the IDP provider. The certificate file must be in text format and have one of the following extensions: .cer or .pm. -
-
Select ALMA (see Alma Information Request Fields), ALEPH (see Aleph Information Request Fields), or SAML from the Select User Information Method drop-down list. The selections for the user information method is based on the ILS that you are using.
-
Select Save to save your SAML profile and to return to the Login Profiles page.
-
Edit your new SAML profile. The Login Profile page will now include the Attributes Mapping button.
The Attributes Mapping button displays only when the user information method has been selected and saved.
-
If you are using Alma for user information, skip this step. Otherwise, select Attributes Mapping to map the user attributes that are associated with the selected type of user authentication. For more information, see Attribute Mapping.
-
Select Save to save your profile and to return to the list of profiles on the Login Profiles page.
-
Create the Primo SAML SP metadata file and send it to your IDP administrator. For more information, see Managing Certificates and Metadata for SAML Authentication.

